SafePay Ransomware: A New Global Threat to MSPs and Businesses
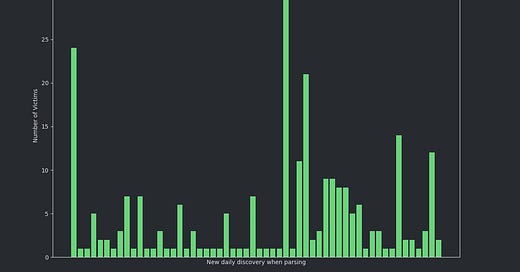
As of Today 7/14/2025: 14 SafePay-Linked Breaches Reported in July
Overview: A Fast-Rising Cyber Menace
In the first quarter of 2025, a cybercrime group known as SafePay emerged rapidly, distinguishing itself as one of the most aggressive ransomware actors globally. According to Acronis Threat Research Unit (TRU), the group has already targeted over 200 victims, including Managed Service Providers (MSPs) and small to medium-sized businesses (SMBs) across multiple industries.
What makes SafePay especially dangerous is its focus on MSPs. Breaching one provider gives attackers indirect access to hundreds of downstream clients, creating a ripple effect. The most high-profile incident so far involved Ingram Micro, a global distributor whose breach caused widespread disruptions across IT service supply chains.
Tactics, Techniques & Procedures (TTPs)
SafePay Operates Independently
Unlike typical Ransomware-as-a-Service (RaaS) groups, SafePay appears to control its own operations, infrastructure, and ransom negotiations. Its attack methods include:
Initial Access: Compromised RDP or VPN credentials
Privilege Escalation: Exploiting local admin rights, abusing CMSTPLUA
Lateral Movement: Living-off-the-Land (LotL) tactics
Defense Evasion: Disabling endpoint protection, deleting shadow copies, clearing logs
Double Extortion: Encrypting files and exfiltrating data for leverage
LockBit DNA
While not a direct clone, SafePay shares technical similarities with LockBit 3.0 (LockBit Black), including:
Fake Windows API calls
38-character password requirement for execution
Encrypted strings and dynamic API resolution
Avoidance of systems in Russian, Ukrainian, and other CIS languages
Use of
ThreadHideFromDebuggerto hinder analysis
Attack Workflow
Initial Access
RDP compromise
Windows Defender disabled
Network scanning via ShareFinder.ps1
Data Exfiltration
Files archived using WinRAR (excluding
.exe,.dll)Transferred via FileZilla, then both tools are deleted
Execution and Encryption
Requires
-pass=flag with a 38-character passwordOptional flags:
-uac(bypass User Account Control)-network(lateral movement)-enc=5(50% encryption)-log(auto.log written to ProgramData)
Pre-Encryption Steps
ACL manipulation
Privilege acquisition (
SeDebugPrivilege)Termination of key processes (SQL, Veeam, Sophos, etc.)
Stopping critical services (e.g., VSS)
Recycle bin cleanup
Registry persistence
Encryption
AES + RSA keypair per file
.safepayfile extensionUses I/O Completion Ports for multithreading
Auto-deletion (
FILE_FLAG_DELETE_ON_CLOSE) for cleanup
Notable Attacks and Victim List Growth
22 Victims in a Single Month
In October 2024, Huntress analysts documented two SafePay cases—each featuring:
.safepayencrypted extensionsRansom note:
readme_safepay.txtNegotiation via Tor and a TON-based messenger
Leak site listing 22 organizations, with downloadable stolen data
Attack Footprint
Targeted countries: USA, Germany, Canada, Australia, Singapore
Industries affected: Business services, education, retail, manufacturing
German victims in construction, transport, and local government listed on leak site
1.2 TB of data stolen from a UK-based enterprise
The Ingram Micro Incident
On July 3, 2025, Ingram Micro suffered a major disruption, taking down their website and order systems. Two days later, the company confirmed ransomware had been discovered in internal systems. The breach was later attributed to SafePay, further underscoring the group’s capability and expanding threat profile.
Triton Sourcing & Distribution: A Case Study
New Zealand-based Triton Sourcing & Distribution confirmed it was attacked in early October 2024, with their darknet listing on SafePay’s leak site showing 10 terabytes of stolen data. A company spokesperson stated:
“It did disrupt our operations for a few days, but we were able to recover relatively quickly... Order details and other operational procedures account for a large portion of this data.”
Although the attackers did not specify the date of intrusion, Triton has acknowledged the breach and the type of compromised data.
Snow Brand Australia Confirms Ransomware Hit
Snow Brand Australia was listed on SafePay’s leak site alongside 23 other new victims. A spokesperson shared:
“We acted immediately to secure our network and initiate an investigation… including any impact to information.”
The group claims to have stolen 24 terabytes of data, including employee Medicare, superannuation, and medical certificate information.
Behind the Scenes: Researcher Discoveries
Researchers identified weaknesses in the group’s infrastructure, including an exposed Apache server status endpoint, which revealed additional backend information from their Tor-based leak site.
Strategic Observations
Decentralized Operations: The group has a lean infrastructure but aggressive reach
TON Integration: Uses Telegram’s “The Open Network” for added anonymity
LockBit Source Adaptation: Features suggest it was heavily inspired by leaked LockBit 3.0 code
Basic Leak Site: Lists victims, claimed earnings, and links to stolen datasets—no frills, just threat
Mitigation for MSPs & SMBs
Experts recommend urgent protective actions, especially for MSPs:
Restrict RDP and VPN access
Implement network segmentation
Conduct employee phishing and threat awareness training
Maintain immutable, offsite backups
Monitor for unusual usage of WinRAR or FileZilla
Regularly update and monitor EDR and antivirus tools
Conclusion: SafePay Isn't Just Another Ransomware Group
SafePay’s rise has been swift and strategically devastating. Its blend of technical sophistication, aggressive tactics, and high-impact targets has placed it at the forefront of global cyber threats. With an expanding list of victims and an evolving infrastructure, it poses an existential threat to MSPs and any business that depends on digital systems to operate.