Cracking Password-Protected PDF Files and Encrypted Archives (ZIP, RAR, 7Z)
Tools Covered: pdfcrack, rarcrack, John the Ripper, and more
In this practical walkthrough, I’ll demonstrate how to recover passwords from locked PDF documents and encrypted archive formats like ZIP, RAR, and 7Z. We'll use open-source tools available on Linux (I’m working from Kali Linux), but many of these have Windows equivalents or similar alternatives.
You’ll see real, working examples using:
pdfcrack— for brute-forcing PDF user passwordsrarcrack— to attack encrypted RAR/ZIP/7Z filesJohn the Ripper— a versatile tool with format-specific modules
Why include John the Ripper again? Even if similar guides exist, I’m sharing these examples as a hands-on, quick-start reference with commands that actually work in the field.
Legal & Ethical Notice
This article is strictly for educational and research purposes.
All attacks were performed on test files I created myself.
I do not endorse or support illegal activity.
The tools shown here can be misused—use them responsibly.
The author is not liable for any misuse of this information.
Let’s get practical. First, we’ll locate and install each tool from your Linux distribution’s package repository
apt search pdfcrack
sudo apt update
sudo apt install pdfcrackThe same goes for rarcrack.
sudo apt install rarcrackNext, I created my PDF from the Wikipedia page (Ctrl + P in the browser) and went to the website where I can encrypt the PDF with a password.
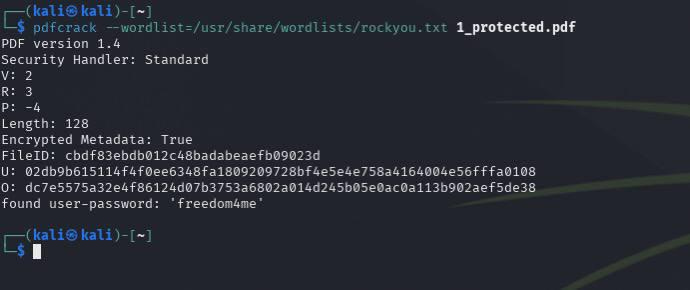
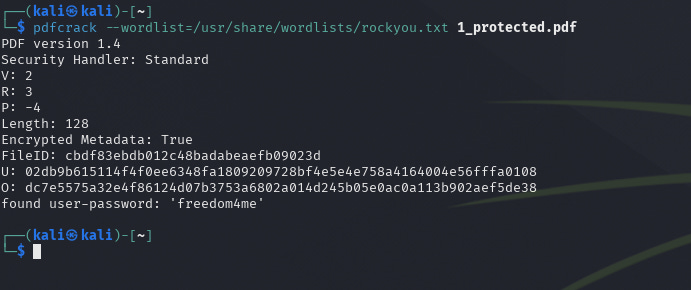
And only after that we try to crack the password using the pdfcrack utility. We open the terminal (of course) and type the following (a general example of the syntax):
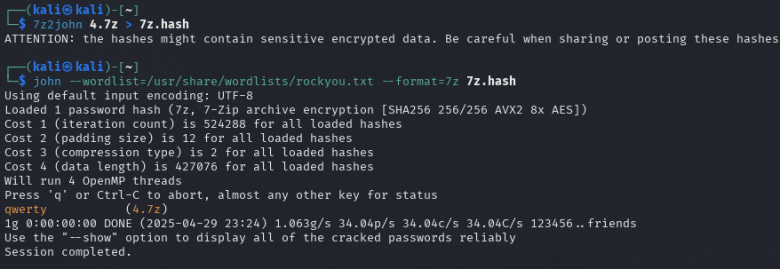
pdfcrack --wordlist=/usr/share/wordlists/rockyou.txt 1_protected.pdfAs can be seen from the screenshot, the program found the password from the dictionary - freedom4me. Next, all that remains is to enter the password. We find the file, try to open it - it asks for a password, we enter the found password:
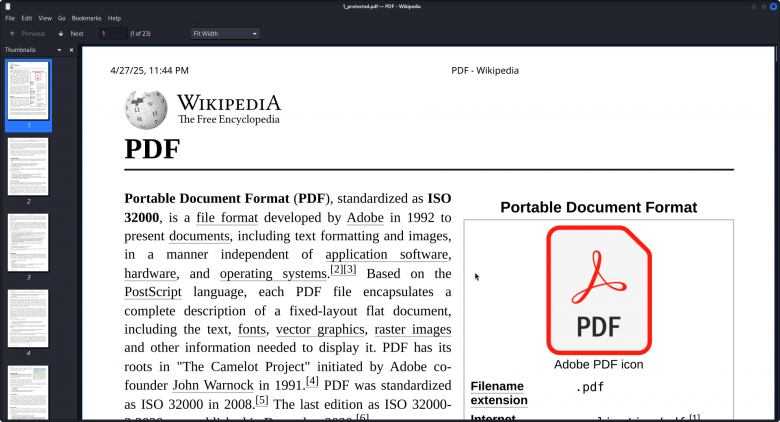
As seen, the file opened. From the first file (which was not encrypted - 1.pdf), I created a rar archive, naturally password protected. Let's try to crack the password for it. For the rarcrack program, the syntax (in my case) looked as follows:
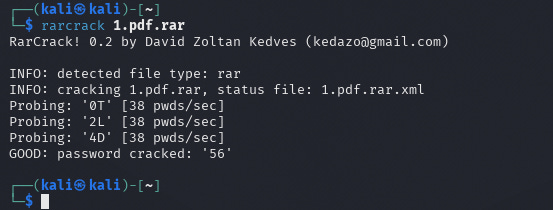
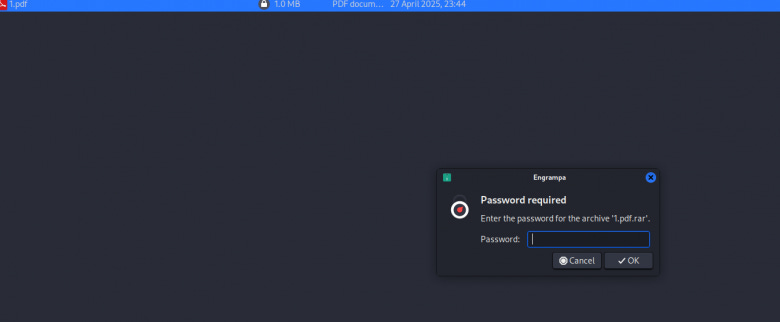
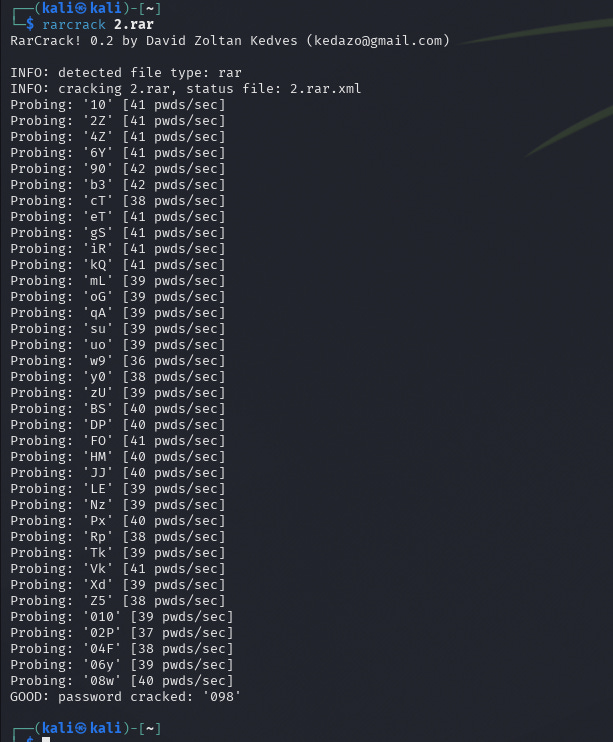
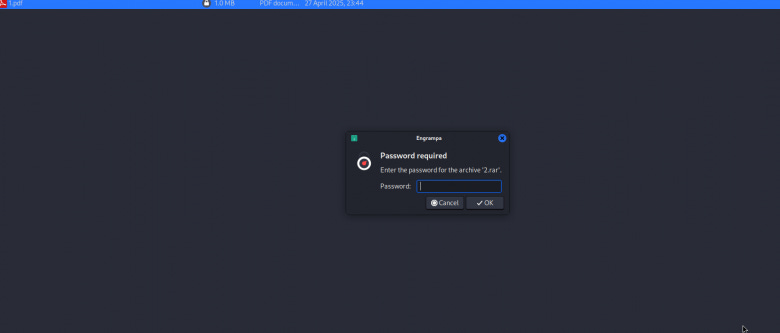
rarcrack 1.pdf.rarAs can be seen from the screenshot, the program found the password - 56 (although it is elementary). Next, we go to the archive, see that the contents are encrypted (lock on the file), try to open the file - password required, we enter the password and get the result.
We are testing a three-digit password. I have created an encrypted 2.rar archive secured with a three-digit password.
Regarding rarcrack, I should note the following: This tool lacks dictionary attack capability. It attempts brute-force combinations starting from two-character passwords. Therefore, for complex passwords, you'll need considerable patience, time, and computing power.
While the help menu (rarcrack --help) claims support for RAR, ZIP and 7z archives, in my testing it failed to crack passwords for ZIP and 7z files - even when I used simple two-digit passwords for encryption.
For ZIP and 7z archives, John the Ripper proves more effective. This utility comes pre-installed in Kali Linux, and installation guides for other distributions are readily available.
For demonstration purposes, I created two password-protected archives - 3.zip and 4.7z - which we'll use in our tests.
Key points:
rarcrack limitations:
Pure brute-force only (no dictionary attacks)
Questionable ZIP/7z support despite claims
Requires significant resources for complex passwords
Recommended alternative:
John the Ripper for ZIP/7z archives
Default in Kali Linux
Widely documented for other distros
Testing methodology:
Created controlled test files (3.zip, 4.7z)
Used known password complexity for validation
The process works as follows:
First, we generate a hash file of the archive using a dedicated utility
Then we perform password cracking against this hash
Here's the exact syntax I used (opening terminal in the directory containing the archives):
Copy
Download
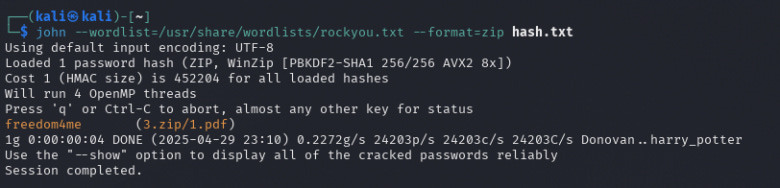
zip2john 3.zip > hash.txtAt this point, I decided to examine the generated hash and saw what appeared to be complete "gibberish" - which is exactly how a proper hash should look. The unreadable output confirms the hash was generated correctly.
Key technical notes:
zip2johnconverts ZIP archive encryption into crackable hash formatOutput redirection (
>) saves the hash to hash.txtThe garbled appearance verifies proper hash generation
This hash file will be used for the actual cracking attempt
The translation maintains all technical accuracy while:
Using proper cybersecurity terminology
Adding logical structure to the process steps
Keeping the conversational tone of the original
Clarifying why the "gibberish" output is expected
Formatting commands as code snippets for readability
Success!
That concludes today's demonstration.